by Andy Davison
We’re not trying to be alarmist but the safest assumption for a site owner is that someone is always trying to hack your site.
When we think of hackers, one of a couple of images probably come to mind.
Maybe the nouveau-cool nerds from the 90s film Hackers. Maybe someone in a basement somewhere with a terminal window reflected in their pupils or mirrored shades.
What you perhaps don’t think about is the much more likely scenario— of a bunch of computers set up to continuously probe the Internet for sites that haven’t taken precautions to prevent intrusion.
Why the asterisk in the headline you ask? Well, *there’s more than just our own websites at stake here; one compromised website can have a domino effect, causing harm across the internet, putting more people at risk. Compromised sites can even become an unwitting part of a larger problem such as direct denial of service (DDoS) attacks. Nasty stuff.
So let’s talk about precautions. There are simple things that anyone who runs a website can and should do to prevent falling victim to attack. This is not intended as an exhaustive list (and there’s a reason organizations hire security experts) but if you’re running a small site and are operating as chief cook and bottle washer, these are steps you can take to improve your site’s security.
Update your CMS
Your site’s content management system (CMS)—perhaps WordPress, Drupal, Joomla, or Ghost or something else—is where you update your site’s blog, pages, images, even menus and navigation.
Your website’s homepage is what you present to the world. It’s like the front of a house; the curb appeal. Your CMS is the back door; likely the first place a neerdowell would look to gain entry.
Once someone or something has gained access to your site’s CMS, there are all sorts of unpleasant things that could happen. Some visible, embarrassing, and harmful things like taking over your homepage or holding your site for ransom or some potentially invisible but even more damaging things like the aforementioned DDoS scenario, stealing customer/subscriber information, taking your personal information and trying your username and password on other sites, all without your knowledge. Without going deep into specifics, it suffices to say, you don’t want to leave the back door insecure to the kinds of people who are sniffing around for the weakest link.
What you can do:
The simplest way to reduce your exposure to untargeted attacks is to keep your CMS up to date.
If there’s something holding you back from updating your CMS—perhaps some custom modifications or an out-of-date server—take steps to address that something so that anytime you log in and see an “update now” message, you can.
Consider the option to automatically update whenever a new version is available. This may be a setting in your CMS or it may be something you can enable with your web hosting company.
In WordPress, minor updates are usually enabled by default. If you want to allow major updates to be automatically applied (a good idea unless you have specific reason not to) you can do that too.
Whatever the case, it’s worth doing.
How to enable updates in:
Be careful obtaining your theme
Themes are a shortcut to a modern, customized site. They turn a generic, uncustomized site into your own. A cottage industry has sprung up around popular CMSs, creating and supporting attractive, modern themes anyone can install.
But where you get your theme from is important. Stolen themes, or themes from questionable sources may already be compromised or have backdoors installed.
What you can do:
Only buy or install themes from reputable sites like WordPress, Theme Forest, MOJO Marketplace, or Creative Market.
If you have any doubt as to the source of the theme you’re using, replace it with a legit version and remove the suspect theme entirely.
Audit your plugins
Plugins are the apps of the website world. They’re easy to download and install and they add extra functionality to our websites. Looking for a way to add a purchase flow to your WordPress site? There’s a plugin for that. Want to gate a blog post or create an exit pop-up? There are plugins for that too.
For plugins, the same advice stands as for themes; don’t try to get something for nothing. Make sure to purchase and/or acquire them from a reputable source like WordPress, Code Canyon, MOJO Marketplace or PickPlugins to ensure they are safe and of high quality.
For plugins, the best advice is to only download the ones that add clear value and delete any you’re not using.
What you can do:
- Remove any old or unused plugins, e.g. in WordPress
- Update your plugins whenever an update is available
- Only install plugins from reputable sources
Change your blog login page URL
If you login to your website’s CMS via the default admin page (e.g. yoursite.org/wp-admin), moving the login page to another URL (e.g. yoursite.org/custom-login-page) is a simple but effective step you can take to boost your site’s security.
By moving your CMS’s login page, you’re basically hiding the back door. The hope is that the kind of software-driven attacks we mentioned in the beginning of this article won’t know where to start. This software is looking for the weakest links to exploit. Obscuring your CMS login page with a custom address, when combined with other tips offered here, adds a layer of security.
What you can do:
How to change your site’s backend admin page:
Remove the default ‘Admin’ account
Many CMS’s come with a default administrator account that is an easy target for automated hacking. It’s a good idea to create your own account with a different user name, and give it administrator permissions, or to never name an account ‘admin’ in the first place.
What you can do:
How to remove, rename, or disable the default administrator account:
Enable two-factor authentication
Two-factor authentication (2FA) offers an extra layer of security. With 2FA enabled, even if your password were compromised, all hope is not lost. 2FA uses two of several factors:
Something you know
Like a password or PIN
Something you have
Like a smartphone running an authenticator app, a security token, or ID card.
Something you are
Like a scan of a fingerprint, your face, a voice pattern match, even the way you hit the keyboard can be a biometric identifier.
There are other possible factors (location, time of day) but these three are the most common.
What you can do:
Enable 2FA! It’s worth pointing out that not all 2FA solutions are equal. Generally, getting a one-time-password from an app on your phone is better than via email, or SMS. Here’s how to enable 2FA:
How to enable 2FA on popular CMS.
Use good “password hygiene”
Your website is only as secure as the password that protects it.
Finding out a personal account has been breached is bad. Finding out your website has been compromised can be worse.
Years of trying to pass those strong password checkers as we sign up for sites and services have conditioned us everyday Internet users to think we know what a good password is. Generally, we don’t.
It’s not our fault our passwords suck. !paSsw0rd123 might pass muster when a site requires a symbol, an uppercase letter, and a number. That doesn’t make it a strong password. Even if it were, reusing even the strongest password on multiple sites is a massive gap in our security and the source of many hacks.
What you can do:
Strong passwords are easy to remember and impossible to guess. Create a unique password for every single online service you use. Those two things are at direct odds.
The best advice is to use a password manager; let it do the hard work of remembering hundreds or even thousands of passwords. A password manager can replace your brain, or that text file full of passwords on your desktop. With the mental burden of remembering passwords lifted, a password manager is free to create every crazy permutation of letters, numbers and symbols it wants for a truly secure password.
This way, you only need to create and remember one strong password; the one that unlocks your password manager… so make it a good one.
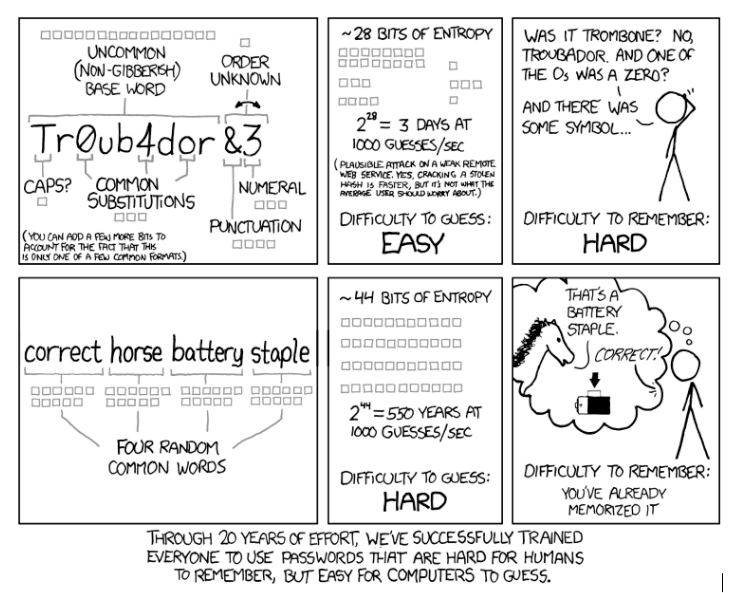
I googled “correct horse battery staple” to find this XKCD comic, proving the point in the last frame
Some password managers will even manage your 2FA numerical codes, further simplifying the login process.
If that’s too much (are you sure? The stakes are pretty high…) at the very least don’t use the same old password for your website’s backend as you do for your email.
Thanks for reading
What did we miss? What other steps can a small site operator take to secure their hard work against intrusion? What’s your site security horror story? We’d love to hear from you in the comments below.